Stuxnet --> From Zero-day to a Destructive Weapon
- Vlad
- Apr 30, 2018
- 5 min read
Before anything else, let's go back in time and check what happened in the summer of 2010..
* June 6 - Rafael Nadal beats Robin Soderling and won 109th Men's French Open.
* June 12 - Premieres one of the most top grossing film in history, Toy Story 3.
* June 17th - LA Lakers won a head-to-head playoffs series against the rival Boston Celtics, winning in 7th deciding games for their 16th NBA title.
June 17th was a full-of-excitement day, the thrills of Game 7 of the Lakers vs Celtics! Sure did one of the most exciting as my fav team won the series in a thrilling game 7. Later did I know that in this very day, is the discovery of one of the most destructive virus ever crafted in history. A virus that could be a possible cause for the next World War...

On the said day, a malware forensic analyst from Belarus named Sergey Ulasen has identified an unusual behavior from one of their customers in Iran who's experiencing an arbitrary Blue Screen of Death and computer reboots. With such symptoms, we can provide a hypothesis that machine could be infected by a virus or just some usual malware. But Sergey believe that it could be something more, as he brought the specimen to a certain 'unknown' security firm at that time, VirusBlokAda. He and his team then realized that what they have is a zero-day. 0-days are vulnerabilities that haven't reached its 1st day yet, a findings that have not been patched and thus unknown to any Antivirus vendors.
But before such historic findings, it was January of 2010 the International Atomic Energy Agency has identified that something was wrong with the uranium enrichment plant in Natanz , central of Iran. A stunning rate of increase of centrefuge was replaced for a year which was unusual compared to the regular average. Investigators had been having a hard time trying to figured out what causing this failure, it would not be physical for the plant has been surrounded by CCTVs. Later did they know that what they're looking for lies on their computer devices. Iran's computer systems has been infected for over year and the malware inside their systems has been silently sabotaging their centrifuges!
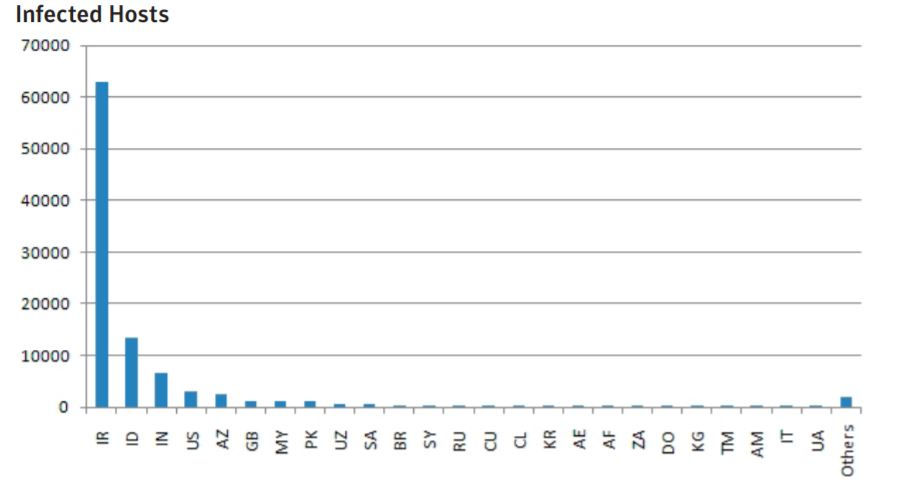
These malware has wrecked havoc on Iran and some other countries, a data from Symantec below for references.
In an interview set by Kaspersky Labs on Ulasen, he described every step on how they uncover this complex variant. With its uncanning capabalities, Stuxnet has the attribute of a rootkit plus a very complexed code. As in his words, I qoute:
"We finally parsed the malware and worked out that it was using zero-day vulnerabilities that allowed Stuxnet to penetrate even well-patched Windows computers. And it was at this point we all agreed the digital certificate had been stolen. Additionally, the complexity of Stuxnet’s code and extremely sophisticated rootkit technologies led us to conclude that this malware was a fearsome beast with nothing else like it in the world, and that we needed to inform the infosec industry and community of the details ASAP."
A beast that even a well-patched Windows can be exploited and stole its digital certificates from Realtek and Jmicron. As per Symantec's Liam O'Murchu,Stuxnet utilized Siemen's default passwords to gain access on programs that runs through WinCC and PCS 7, that controls and modify the code of the Programmable Logic Controller that are then used to manipulate machines.
Static Analysis - How did it get there?
Stuxnet cycle began with its intial main dropper WTR4132.TMP, which is a DLL file loaded by explorer.exe. Let's further dissect this dll file..

File masquarades as .tmp file, but seems to be a dll file. We then verified that the detection ratio is extremely high.When executed, it will find and search for the '.stub' section('stub+net' - where the word Stuxnet came from) of the code. Here's what we got on the .stub section

After loading the stub section, it would then hooked to ntdll.dll, which is an interface to Windows kernel. Executables generally do not import this file directly, but when it does, it means that the attacker would use features that cannot be loaded on Windows. Tasks like hiding functionalities and manipulating processes will use this loader. Furthermore, functions hooked in to ntdll are as follows:
*ZwMapViewOfSection- routine maps a view of a section into the virtual address space of a subject process.
*ZwCreateSection - routine creates a section object
*ZwOpenFile - routine opens an existing file, directory, device, or volume.
*ZwCloseFile - routine closes an object handle.
*ZwQueryAttributesFile - Retrieves basic attributes for the specified file object.
*ZwQuerySection - Retrieves information about a section object.
These 6 APIs, once loaded by the mentioned dll, GetProcAddress will then be executed to seek for the address of a certain file export from a dll and when called, it would create a new handle for a new dll file.
Once this trojan/worm has been executed, it would project to process (1)a series of lsass.exe will be generated and will run on the background and (2)with ZwCreateSection, it will create a new PE section in memmory space.
In (1)
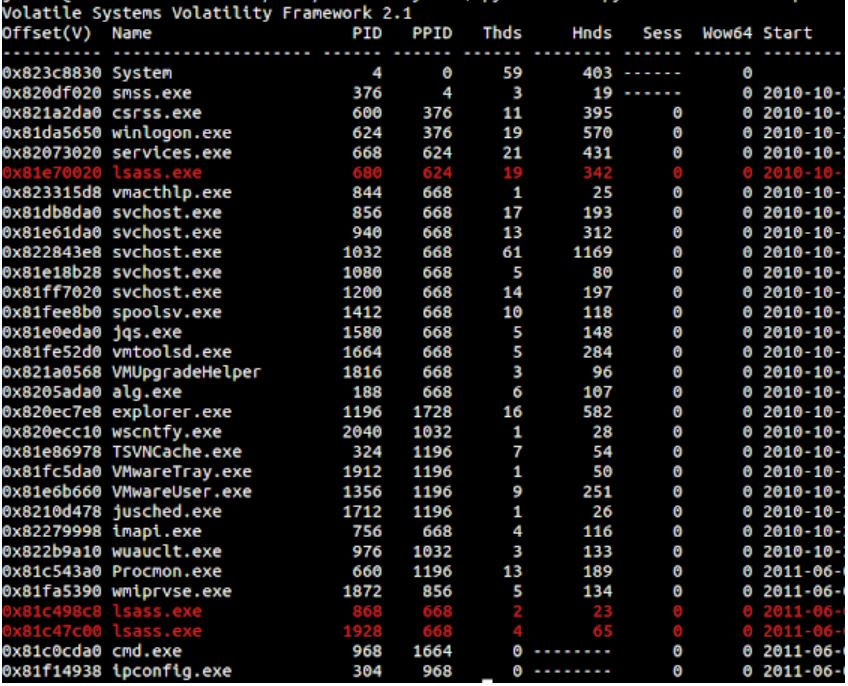

After the process execution, the applied process will create a new file indicated below.

A creation of session under Netbios TCP/IP with the attached GUID adaptor. A new .tmp file will be open, next, refer to the screenshot below.
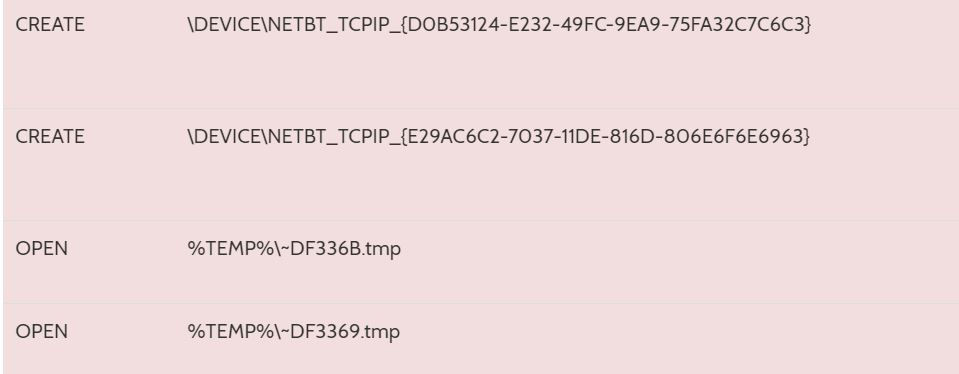
With the identified file loaded, below is for further information..

On (2), that is the creation of a new PE section. It would then get the module handle through LoadLibraryW API. Thus, execution would lead to loading of this DLL files:
%System32%\drivers\mrxcls.sys
%System32%\drivers\mrxnet.sys
%Windir%\inf\mdmcpq3.PNF
%Windir%\inf\oem6C.PNF
%Windir%\inf\mdmeric3.PNF
%Windir%\inf\oem7A.PNF
With mrxcls.sys and mrxnet.sys already dropped on the host , it would then install these drivers in the registry to make sure that these will run everytime the system boots.
Stuxnet is now installed on the target.
Difference with any other virus code
Security Researchers has confirmed that this type of worm+rootkit has been the most sophisticated. The ability to adapt when it hooks in to a certain system, by being dormant and self-learns the security system installed on the target. With its advance capabilties, once it achieve to evade detection on the host's security system it will now perform its attack.
A centrifuge is a basic tool needed to refine uranium. Siemens, offers the best built of centrifuge in the industry. Stuxnet then manipulate the Siemens' controller by forcing the machine to spin until they destroy themselves. When a uranium component was inserted in a Stuxnet-controlled centrifuge, the worm will do its job to perform a faster spin until the machine gives up, and stop. Thousands of machines where infected, as the worm payload has the capability to falsify the readings and made it appear that operation is well and performance is within the expected parameters. Thousands of machines where 'quietly' destroyed. And this doomed out Irans' Nuclear dream.
So, who's behind this?
In a German magazine, Edward Snowden revealed that Israel and NSA(USA) co-wrote this massive attack. The goal was to break the Iranian centrifuge by doing so both governments(Israel and US) hope to set back the Iranian research program, as the US hoped to keep Israel from launching a pre-emptive military attack.The well known "Operation Olympic Games" was started during the George W. Bush reign and continued until Obama's. There are several conspiracies regarding this conspicous subject, but this is the one the shines most.Neither parties did not admit, but who knows when could be the next attack as destructive as this piece. A new form of bomb is on its rise.
What's next?
Stuxnet did marked up history, with it being the first of its kind for the future of warfare. It has just began, the new age of revolution, could be the next World War. It is a kind of weapon so silent that it leaves no trace. It can destroy a certain more effectively than a typical explosives. Its ability to self delete, would leave the target doubt themselves.
References:
Stuxnet Malware Analysis Paper by Codeproject
W32.Stuxnet Dossier by Symantec
Zero days, a film Documentary by Alex Gibney
<krontek>halt


![[CodeWithMe]Bruteforce and Decrypt Cipher in Python](https://static.wixstatic.com/media/fcac84_ba39d510201e40439132a37e4eb000e9~mv2.png/v1/fill/w_980,h_551,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/fcac84_ba39d510201e40439132a37e4eb000e9~mv2.png)
![[CodewithMe]Create your Packet Sniffer(ExploitDev)](https://static.wixstatic.com/media/fcac84_3b8c6fd32f9e45feb2c7b87850ff5974~mv2.png/v1/fill/w_980,h_551,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/fcac84_3b8c6fd32f9e45feb2c7b87850ff5974~mv2.png)
Comments