Tesla - The Walkthrough
- Vlad
- Feb 11, 2018
- 3 min read

Last week I have introduced and provide you some feautures on Tesla. On this post my goal is to show you some tests on how this application really work, how can it detect and provide remediation on the identified threat. To go to my last blog on this, you may proceed with the l
https://kenciceron45.wixsite.com/krontek/home-1/tesla-a-universal-malware-repository-scanner
>Launched
As we launched through the app, it will prompt you the last time the Universal Malware Repository has been updated. It will also let you know the last time your system has been updated. And with the last line contains recommendations on what the user must do.

>Menu Options
After pressing any key to continue, you'll see a simple <Tesla>where you are prompt to input a command. This is were you jat down what will the app do for you. Right now, typing in command 'help' will show you what commands you'll use to operate this AV scanner.

>Menu Option - Settings
Typing in settings will give you 2 options as of now, either to perform scheduled scan on the system or update your AV.
~~Scheduling a scan
Setting up a scheduled/routinely scan on your host is a must. This is like visiting your doctor for a regular check-up, but in this case it must be more-regular. It is advised that a certain AV must protect its host as long as its powered on. Malware persistence, browsing the net, and running some unwanted application are the problematic factors the AV must face. So let's get it a go and protect our system, by typing in settings and choosing Schedule a scan from the menu. Then, it will let you choose to what frequency the scheduled time would be.

So, let's say we set the scan to daily. We are then prompt, to set what time of the day we want the host to be scanned, thus we can also have a choice to scan a certain folder or the entire disk.

~~Updating Signature
In settings, we'll also find option to update the virus scanner signature. We normally can see the status of the application if in its latest sig or not once we are in the intro page. Thus, in this case it seem that the signature is not up to date, so we need to have the latest sig installed.

To do that we need to go to settings and choose '2', to update to the latest sig.
We are then asked to input the complete malware db location.

Then after that, AV will now proceed with the update and once done will then prompt the user to proceed to main.
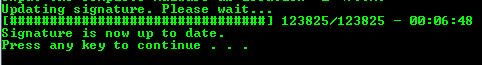
We can now see that our scanner is already on its latest sig, and our host is now protected.

>scan dir
With its signature up-to-date, we are then confident that our system is safe. And with this we can now proceed with the scan. I have a sample folder containing a dropped malicious file. File lies on disk F: and contain some other file with it.

As shown on the scanned results, vt_input_other.txt is the malicious binary, and the remaining 3 files are clean. Also decided to isolate the malicious file, and put it on a separated pane. Right now, I decided to have the detected file to be deleted, but as for the next version will make room for quarantined file.
Below is the scanned results for entire D drive.

Conclusion
I sum up this version as an AV scanner which utilized a universal malware repository. As I am working on my second version of Tesla, I am working my best to have a complete AV functionality, in a way that it will have its real-time host monitoring and protection. Action for file quarantine and cleaning must also be implemented for there can be times that suspected file is not recommended for deletion as it is used for production, thus we only need to have the file deleted and quarantined. File infected with malware capable of malicious code injection must also be identified and cleaned, for this must be detected by the real-time threat detection. With all this mentioned, I'll keep you updated for the next version.
<krontek/tesla>exit



Comments